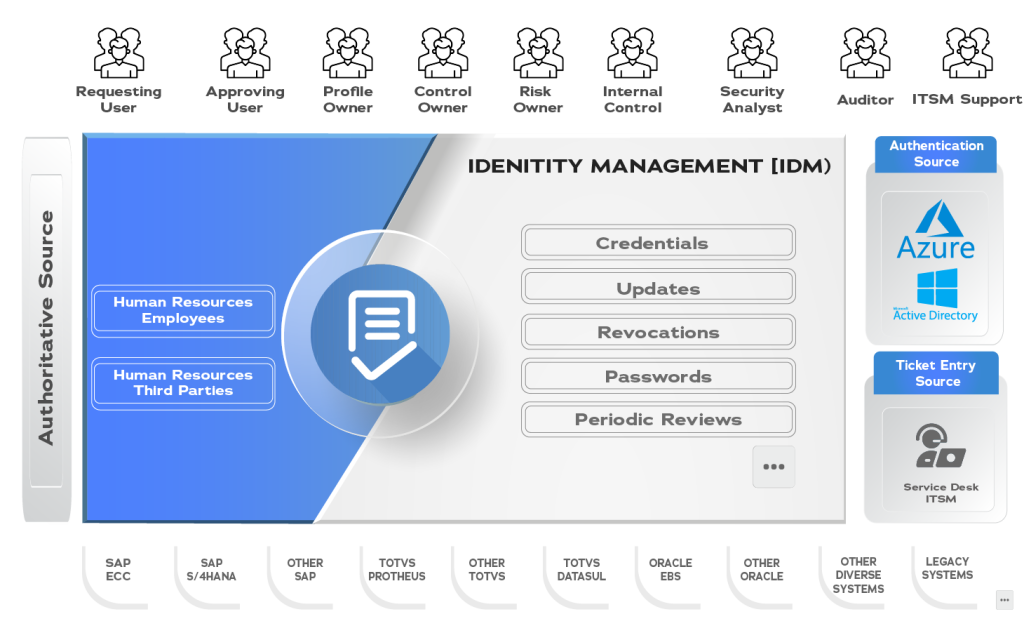
IDENTITY MANAGEMENT
Identity lifecycle: organized and secure management from start to finish
Our Solution
IDENTITY MANAGEMENT
Developed by experts
- Highly scalable identity management;
- Intuitive self-service request interface;
- Holistic view of access for intelligent role management;
- Allows integration with Flows for risk analysis of segregation of duties (SoD);
- Systemic process of periodic access reviews;
- Compliance with SOX, CVM, IBGC, and other regulations;
- Two-factor authentication (2FA) via SMS, email, WhatsApp, tokens, among others;
- Single Sign-on (SSO) authentication;
- Speed of implementation and return on investment.
FEATURES
Designed by experts with extensive experience in the Management and Identity cycle and processes.
Flows
Flexible workflows that easily adapt to the most stringent business, audit and security requirements. Ensure compliance and security of your processes.
Security
Allows user authentication via Single Sign-On (SSO) with two-factor option (2FA). All communication is protected by the SSL protocol, ensuring the highest level of security.
Integration
Integration with multiple platforms, systems and processes, allowing governance of identities and access to all systems integrated into the platform.
Effective Control
Strengthen the identity and access lifecycle with preventative governance policies to protect your organization from creation to revocation of access permissions.
Quick View
In no time, you can establish an identity and access governance process and take steps to mitigate risk, avoid audit non-compliance.
Monitoring
Intuitive dashboards that provide a consistent experience for users and administrators, enabling detailed and effective analysis of the entire identity and access lifecycle.
INTUITIVE INTERFACE
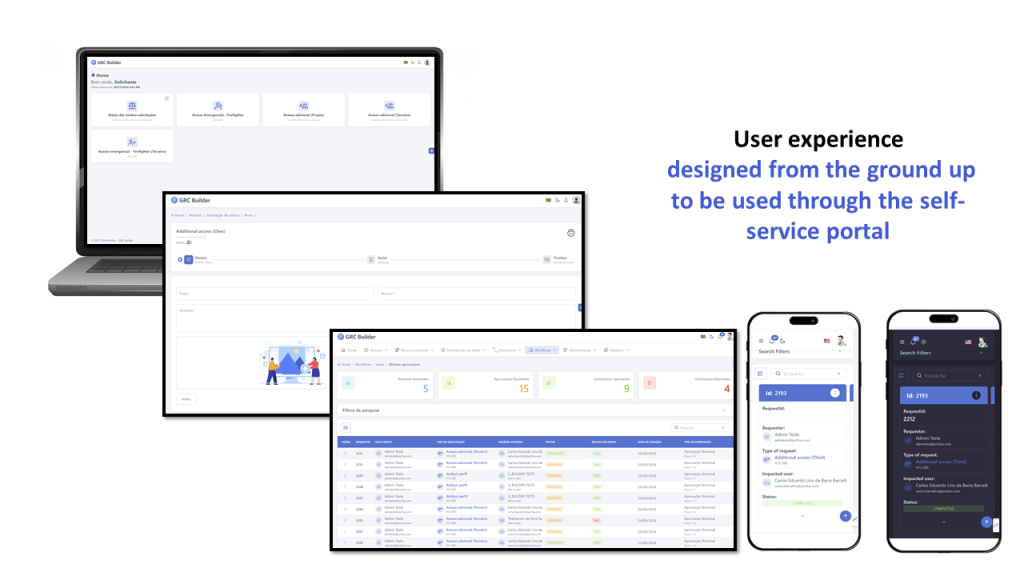
User experience designed from the ground up to make it easy to use and govern the identity cycle.
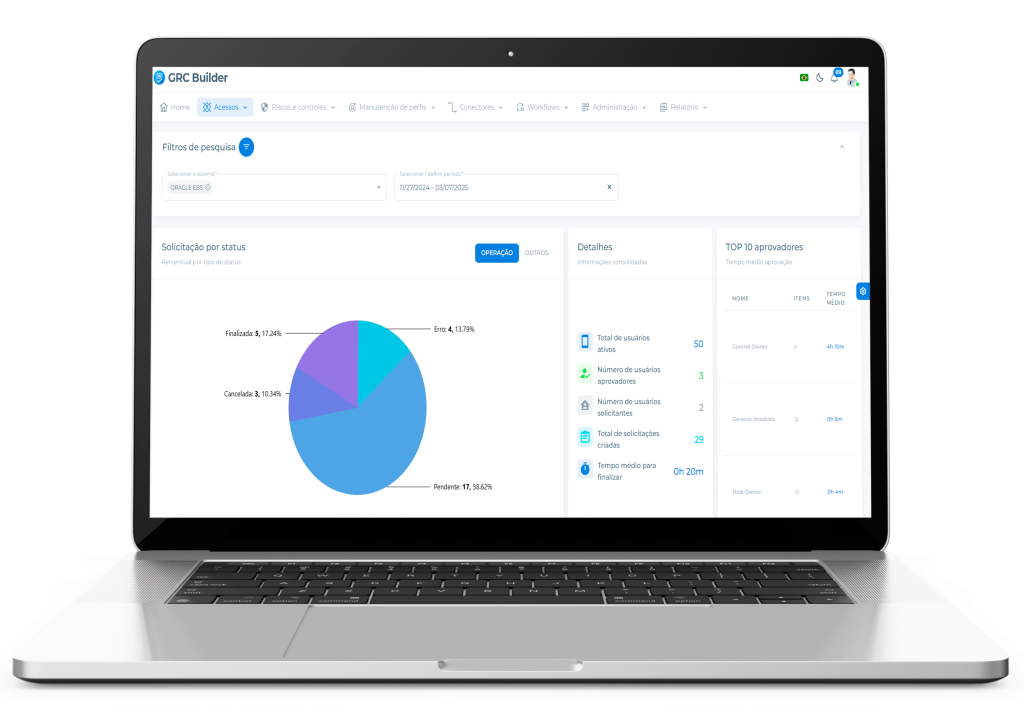
Monitoring Dashboard – Holistic View of Access Requests
Our Monitoring Dashboard offers a comprehensive and centralized view of all access requests, providing full transparency and control throughout the entire approval cycle. With it, you can monitor in real time the status of each request, whether approved, rejected or in progress. This holistic view allows you to quickly identify bottlenecks, optimize flows and ensure effective governance, ensuring that each decision is well-informed and aligned with security and compliance policies.